Inferring Sensitive Information in Cryptocurrency Off-Chain Networks Using Probing and Timing Attacks
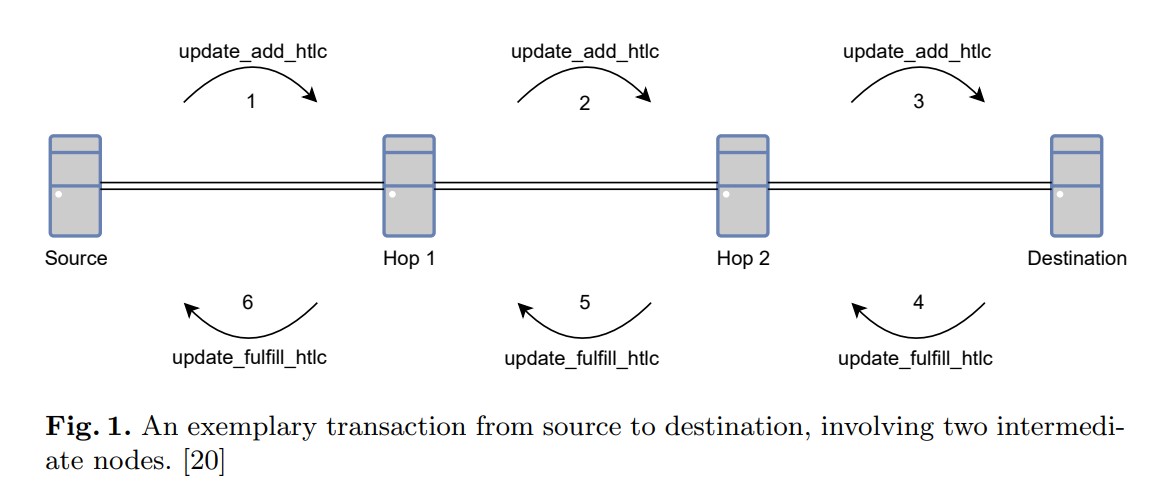
Off-chain networks have recently emerged as a scalable solution for blockchains, allowing to increase the overall transaction throughput by reducing the number of transactions on the blockchain. However, off-chain networks typically require additional bootstrapping and route discovery functionality to determine viable routes. For example, the Lightning Network (LN) uses two mechanisms in conjunction: gossiping and probing. This paper shows that these mechanisms introduce novel vulnerabilities. In particular, we present two attacks. The first one, which we shall call a probing attack, enables an adversary to determine the (hidden) balance of a channel or route through active probing and differentiating the response messages from the route participants. The second one, which we shall call a timing attack, enables the adversary to determine the logical distance to the target in hops, given that geographical data of LN nodes is often publicly listed, or can be inferred from allocated IP addresses. We explore the setup and implementation of these attacks and address both the theoretical and practical limitations these attacks are subject to. Finally, we propose possible remediations and offer directions for further research on this topic.
 Top
Top
- Nisslmueller, Utz
- Foerster, Klaus-Tycho
- Schmid, Stefan
- Decker, Christian
 Top
Top
Category |
Book Section/Chapter |
Divisions |
Communication Technologies |
Subjects |
Angewandte Informatik Rechnerperipherie, Datenkommunikationshardware |
Title of Book |
Information Systems Security and Privacy |
ISSN/ISBN |
978-3-030-94900-6 |
Page Range |
pp. 1-21 |
Date |
1 January 2022 |
Official URL |
https://link.springer.com/chapter/10.1007/978-3-03... |
Export |
 Top
Top